 |
||||||||||||||||
 |
||||||||||||||||
 |
||||||||||||||||
 |
||||||||||||||||
|
||||||||||||||||
 |
||||||||||||||||
 |
Counter / Strategies |  |
||||||||||||||
| Today the decision on which criteria of an image or better of its transmission (in the sense of performative strategies) perception of authenticity relies obviously has been becoming more important than its depiction. Thus the view on perception frames the depicted image. It is astonishing how widely strategies of framing or sequentional repetition are used now to bring something within a reality context, thereby demanding for authenticity. Performative strategies are introduced into most mediated spaces. | ||||||||||||||||
|
'... That the mechanisms of performative power are nomadic and flexible
more than sedentary and rigid, that its spaces are networked and digital
more than enclosed and physical, that ist temporalities are polyrythmic
and non-linear and not simply sequential and linear.' J.McKenzie 'perform or else' |
||||||||||||||||
| H.Farocki explains and imitates
in his filmic essay 'eye/machine' the strategies of electronic sight.
(info at crtl
[space] or new filmkritik
and in english Eye/Machine) |
Examples for different strategies to produce a countersight: |
|||||||||||||||
|
|
Ranging from
political scenes to private webcams. It is already a common approach,
used by artists up to real-life documentary reporters, to record in
an amateur-like handheld camcorder style. Ultimatively an event becomes real, when low-quality amateur material can be transmitted via one of the big news channels (TV and internet). Some similarity can be seen in the increasing use of videomaterial especially of surveillance cameras in various media contexts. They mainly show no other evidence then the imprinted timecode. |
strategies of explaining the construction of authenticity /visibility: | ||||||||||||||
| - Lisa Parks:
Orbital
viewing - Harun Farocki (see also image above) - FAS: looking on official material and opinions - Public Eye: making new use of it - Remote sensing tutorial |
||||||||||||||||
|
|
||||||||||||||||
| The
surveillance camera players (scp)
perform their pieces in front of the invisible audience of surveillance
cameras. |
||||||||||||||||
| strategies of inversing and subverting technology: | ||||||||||||||||
 |
Naturally all
these strategies of producing a certain visibility and thereby as
well invisibility carry the inherent possibility of inversion. The
problems for this tactics obviously dwell in access, cost/money, mobility,
... so therefore it very much relies on identity, which usually just
gets constituted through visibility. Information technology is highly political, but its politics are not directed by its technological features alone mentiones J.Fiske. |
- Paper
Tiger TV (using different and low-tech technics) - Bureau of Inverse Technology - N.Nisbet (tracing virtual identity see: 'Pop. Goes the Weasel') - Jordan Crandall |
||||||||||||||
| strategies of disturbance: | ||||||||||||||||
| 0100101110101101.org
use strategies of subversion to make things obviously. This is their
logo of a new GPS project. |
They are made by social means which are deeply incorporated in the process of translating information into knowledge. | - Surveillance
Camera Players (> image) - EDTheater (also image) - about Culture Jamming, in general jamming and as an example rtmark |
||||||||||||||
 |
The accessability
of electronic tools, like camcorders or internet, radically changed
the situation in many parts of the world. which dictate possibilities
and difficulties. People interested in political and social circumstances, as well as artists, are making use of the invented technologies combining them with their specific possibilities. Their strategies have to deal with widely spread and established concepts. |
|
||||||||||||||
| strategies of irony: | ||||||||||||||||
| - H.Bunting:
CCTV - Fake - Afghan Explorer |
||||||||||||||||
|
|
||||||||||||||||
| strategies of acess and information: | ||||||||||||||||
| The ascii
art ensemble converted whole films to ascii code, displaying also
an underlaying grid. (deep
ascii) |
So immediate
ways of use have to be considered. Interestingly two main strings can be notified as being adopted, which are performative procedures and the introduction of viral methods. Both using the nomadic and flexible mechanisms, as well as polyrythmic and non-linear temporalities, which are corresponding to the caracteristics of new media. Performative structures work with the creation of frames of representation and concepts of perception. They span from decontextualisation, fake, to the simple use of low-tech equipment. |
- documenta x) - NYC Surveillance Camera Project; iSEE - BIG NOISE TACTICAL or videoactivism - safercity.de |
||||||||||||||
 |
and also
to mention just a few projects like: - indymedia - electronicintifada |
|||||||||||||||
| and at least
something in general on tactical media: - ongoing discussion at nettime link 1 / 2 - - the ABC or also in contentwire |
||||||||||||||||
| The Electronic Disobidience Theater (EDT)
brings together strategies of disturbance and subversion. |
Still this is considered authentic because of the presumed lack of it's user's to resources to intervene in its technology. Equally fluid in influencing a situation is the disposition of viruses and it is just this intention of disturbance, which marks the effects and not its appearance. Both ways naturally can be inversed too, as to be seen in the text source of D.Dion and as mentioned before. So this just adds one more uncertanity to the constant shift in the construction of perception, but it also can be taken as a chance to step beyond predefined visibility and categorized sight. | and: - digitalcraft |
||||||||||||||
 |
||||||||||||||||
|
It is quite clear that the situational context has become more important for the presentation of images. A further confusing point has been added through the fact, that almost everyone and every media is incresingly using performative strategies. Though today this is the only way to establish meaning through these images of delegated perception in the traditional system of sight. |
||||||||||||||||
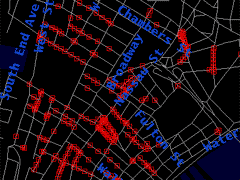
| The Institute for Applied Autonomy i SEE provides a website showingl Manhatten surveillance cameras and a map to avoid them. | more at: download thesis. | So to mention is the new status images should gain. In any case it has to deal with fluidity - one single image says nothing within an machinc assemblage. | ||||||||||||||
|
|
||||||||||||||||
 |
||||||||||||||||
 |
||||||||||||||||

